Threat Part 4: Capability
Part 3 of this series provided an overview of a threat development process. It talked about capabilities but did not go into detail. This part will focus on capability identification. It is not as straightforward as one might think. Looking at some of the capability sites on the web, such as How Do You Actually Measure Military Capability? Many sites equate capability with equipment. But it is much more than that. And it is a convenient shortcut that may generate misleading results.
For example, compare Germany and France in 1940. France had more tanks, and possibly better tanks, than Germany. They also had the Maginot Line, which should have channelized the German attack. Yet the Germans tore through the French in a matter of days. Which side had the better capabilities? Given the lopsided outcome, we’d have to say the Germans. Yet the equipment-based capability before the war says France had far greater capabilities.
The difference is two-fold:
- Doctrine. France and Germany had different doctrines. France tied the tanks to the infantry. Germany tied the tanks to maneuver, designed to achieve a breakthrough and let the infantry secure the terrain gained in the breakthrough. France relied on terrain and fortifications. The two nations learned different lessons from WWI.
- Skills. Skills = ƒ(training, time, resources, trainers) at both the individual and organization levels. Germany spent a great deal of time, much of it in the Soviet Union to circumvent the Treaty of Versailles restrictions, training on their doctrine and honing their skills at all levels from the individual through the division level. They used the invasion of Poland to prove their doctrine and skill sets. France, relying on terrain and fortifications, did not spend as much time and resources on training. An organization can spend a great deal of time and resources on ineffective training that does not create effective skills.
Capabilities are multidimensional. An airborne battalion is not a capability. It is a tool for manifesting capability. For example, forced entry is a capability that can employ an airborne battalion.
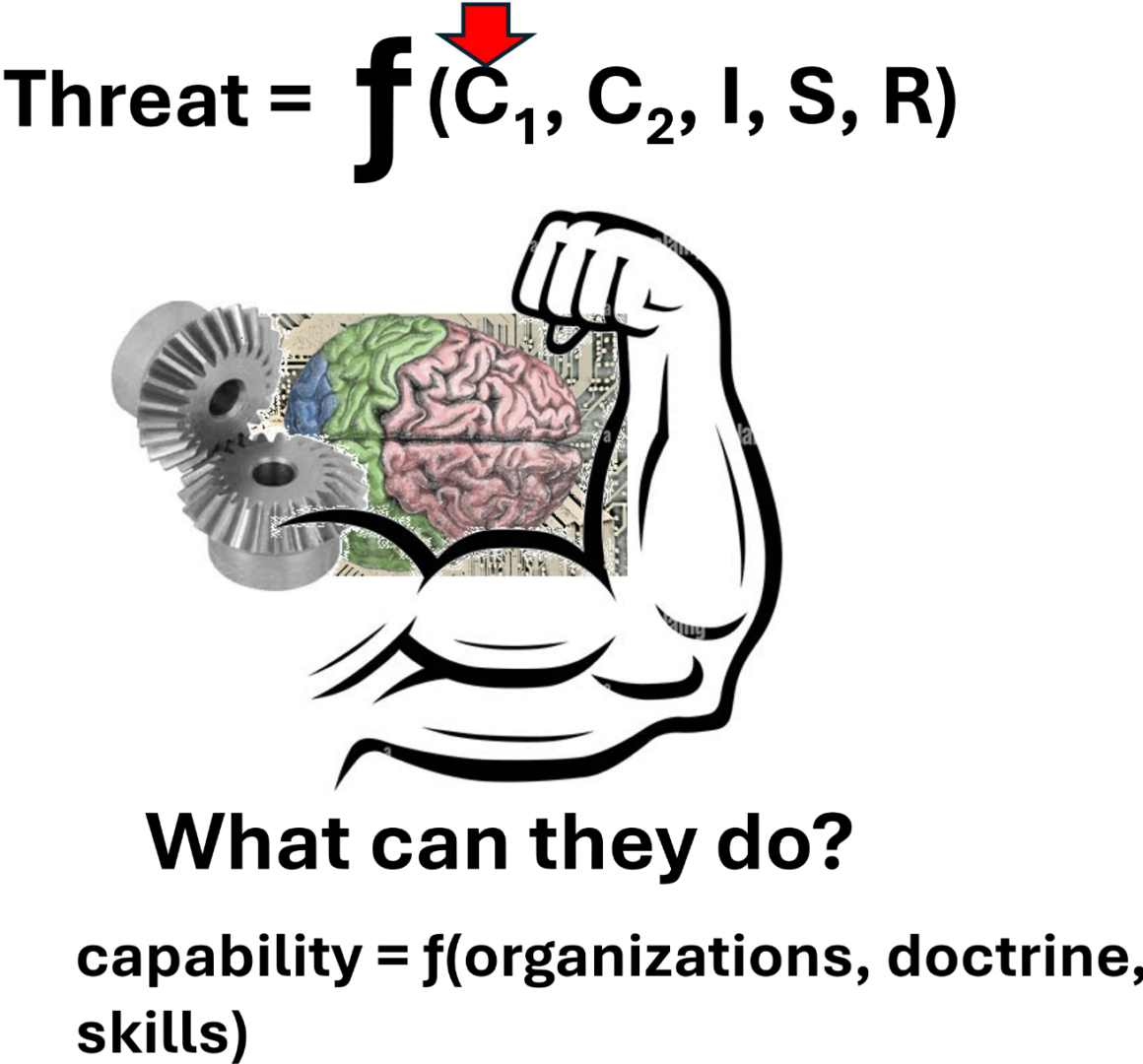
Perhaps we can create a capability function state like
Capability = ƒ(organizations, doctrine, skills).
Organizations are a function as well.
Organization = ƒ(people, equipment, command and control (C2) and tactics, techniques, and procedures (TTP)).
Broadly speaking, there are two ways to determine threat capabilities:
- Part 1 noted that intent influences and shapes capabilities and capacity. We can examine the threat intent and then determine the capabilities they will need to realize their intent.
- Build a library of capabilities and then determine which capabilities can apply to the threat regardless of intent.
Therefore, threat analysts, during the Analyze Information function, need to group the elements of capabilities and determine whether the threat can manifest a capability. I suspect this is as much an art as it is a science. Perhaps that is why some measures of capability rely on the potentially single dimension of equipment since it requires only the quantifiable concept of equipment. Threat analysts need to be as much of an artisan, understanding the nuances of doctrine and training, as an engineer, evaluating organizations’ equipment and weapon systems.
Given the potential uncertainty in the capability function, threat analysts need to consider a capability spectrum. Even organizations within the same overall organization may have significantly different training levels. For example, when I was a rifle platoon leader in the 82nd Airborne, our 3rd platoon constantly got lost and had breaks in contact with the rest of the company. During our company ARTEP, they were completely lost and never took part in the night attack.
So, let us look at a potential example of threat capability identification. In this scenario, China intends to invade Taiwan and assimilate the island into China.
| Key Tasks | Capabilities |
| Conduct forced entry |
|
| Disrupt Taiwan reactions |
|
| Prevent the US and others from intervening |
|
Once analysts identify the capabilities, they first go into the capabilities library and see if any capabilities are already defined. If there are, the analyst then determines if the capability definition with organizations, doctrine, and skills fits the threat or needs to be modified. For example, the conduct beach landing may have a Russian organization and doctrine, and we are modeling China and therefore need to create a new library entry with Chinese organizations and doctrine.
Since doctrine and skills assessments are often more qualitative than quantitative, they need assumptions that analysts must test to validate their ratings.
Likewise, analysts must assess the organizations, both for the elements in the organization function statement [ƒ(people, equipment, C2, and TTP)] and for the consistency of the elements across the spectrum of the same organization type.
Capabilities and the threat’s ability to employ them may vary widely within the same threat. Trainers, war gamers, and experimenters need to recognize this and ensure threat analysts continue to update and validate assumptions and their threat assessments.