The Angel Oak: Nature, Nurture, Or Something Else: Implications for Free Will
Note: I try to meditate nearly every day. Often, I will get a thought during meditation that acts like a seed for follow-up contemplation. This is an example. I started out with a meditative seed on the Angel Oak and…
Insignificant in the Cosmos, Critical Where We Stand
I had an interesting insight during my morning meditation. It’s certainly not too original or impactful. But for me, at this time, it was revelatory. One person standing in the vastness of the cosmos is relatively insignificant. But that same…
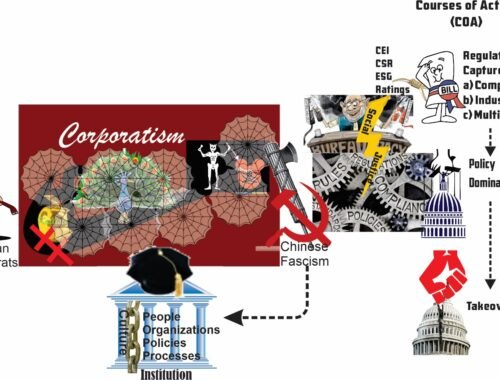
Was our Culture Intentionally Disrupted and Broken, Part 2
“When you have eliminated the impossible, whatever remains, however improbable, must be the truth.” – Arthur Conan Doyle, physician and writer of Sherlock Holmes Part 1 ended with the questions: Why is this happening? What are the disrupters’ objectives? Threat…
Threat 8a: Because That is where the money
Is Willie Sutton is most often credited with replying, “Because that is where the money is” when asked why robbed banks. Sutton denies he said that. Quote Investigator attributes the statement to Paul Perritt, who was 26 years old when he…
Threat 8: Risk and the Threat
Part 1 framed the fundamental risk question as “How much risk and what kind are they [the threat] willing to take?” This concept underpinned the Cold War concept of Mutual Assured Destruction (MAD). While MAD appeared, well mad on the…
Was our Culture Intentionally Disrupted and Broken, Part 1
The first step in community organization is community disorganization. The disruption of the present organization is the first step toward community organization. Present arrangements must be disorganized if they are to be displace by new patterns…. All change means disorganization…
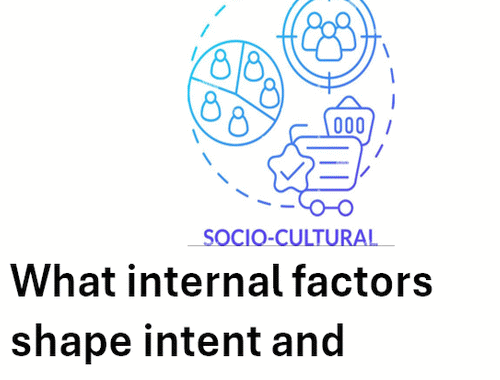
Threat 7: Sociocultural Aspects of the Threat and Strategy
“Culture eats strategy for breakfast,” a quote often attributed to Peter Drucker, highlights an undeniable truth: Even the most brilliant strategy can falter if not supported by a strong, aligned leadership culture. The key sociocultural question framed in Part 1…
Threat Part 6: Intent- Needs, Desires, and Fears
What the threat wants to achieve is a function of desires, needs, and fears: Intent = ƒ(desires, needs, fears) There is a theory that if people and nations just understood each other and could clearly see their motive, needs, and…
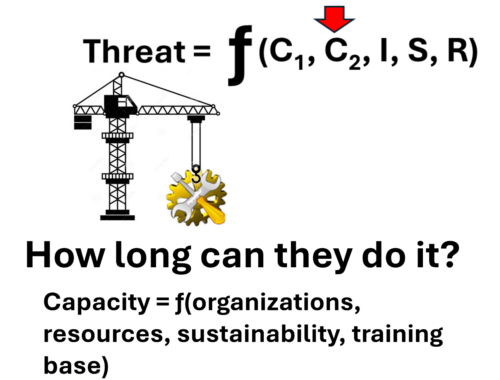
Threat Part 5: Capacity
With capacity, the fundamental question is: how long can the threat sustain capabilities? Do they have the capacity for just a single strike or do they have the capacity for multiple strikes and to sustain the capabilities over an extended…
Threat Part 4: Capability
Part 3 of this series provided an overview of a threat development process. It talked about capabilities but did not go into detail. This part will focus on capability identification. It is not as straightforward as one might think. Looking…