Threat Part 2: Component Integration
Part 1 of this series developed the core threat components and noted that they pertain to all organizations, whether military, commercial, educational, charitable, non-governmental (NGO), or political.
The components in the function statement:
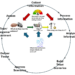
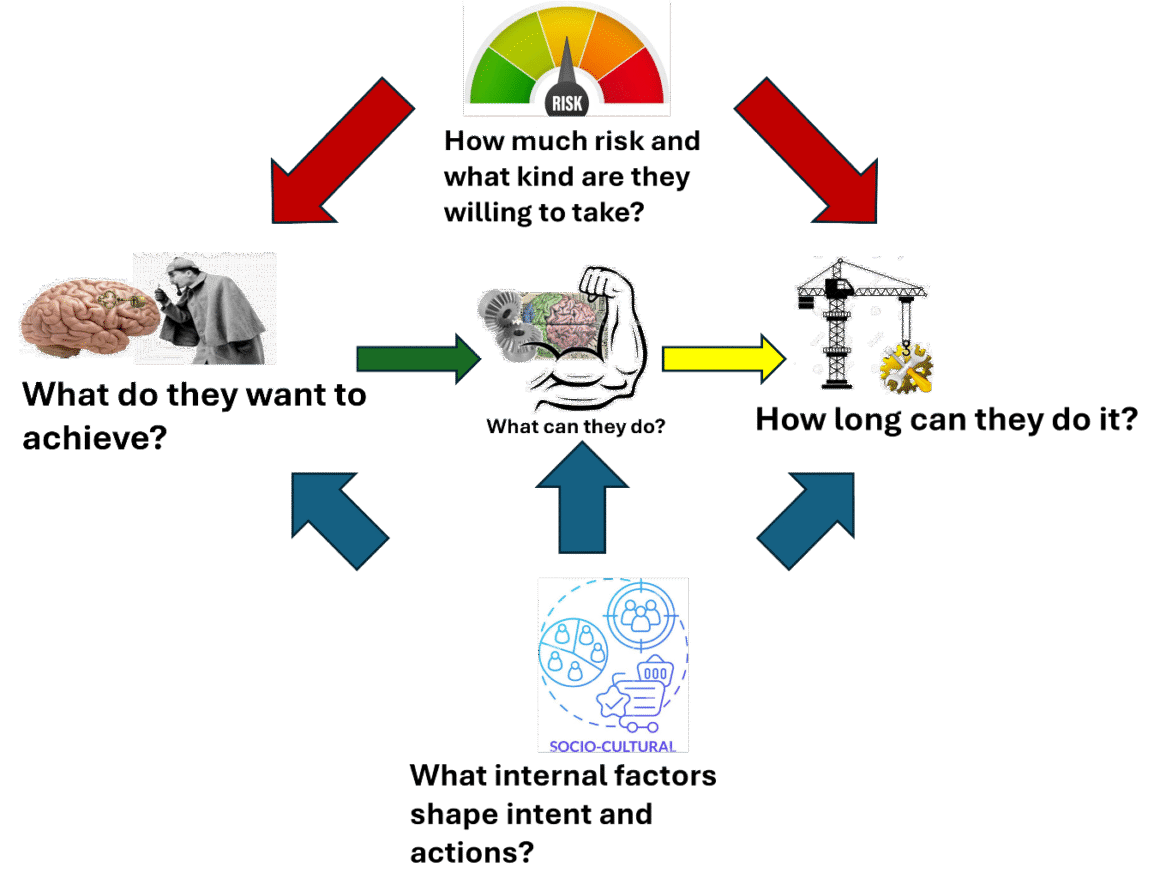
Threat = ƒ(Capability, Capacity, Intent, Socio-cultural, Risk)
are interrelated and influence each other as the diagram shows. While the arrows are one-way, they can sometimes be two-way. For example, as a threat develops capability, and as socio-cultural/political conditions change, they can change intent: what they want to achieve. A case in point is China. As they develop stronger area denial and power protection capabilities and as they distract the US via socio-economic activities and conflicts they sponsor elsewhere, their intent for Taiwan can change.
Socio-cultural and risk are the most malleable components of the threat. New technologies, equipment, and doctrine can mitigate risks. Changing socio-cultural movements can change the assessment of a risk. Socio-cultural changes and approaches may also generate capabilities. For example, were the Chinese Confucius Institutes that were rampant on American campuses a threat capability? Did they attack American socio-cultural traditional values and hence undermine American capabilities? These institutes are largely gone from US campuses, but are they really? Did they just go deeper underground? Did they plant seeds that are still sprouting?
The Confucius Institute example also shows the relevance of the threat analysis across multiple organization types. I suspect that in today’s environment, education, charities, and NGOs have political overtones. In my paper, “Can Non-state Actors be a Collective Moral Agent that can be Ethically Responsible for Its Actions-Ethics and International Affairs,” I argued that many of these organizations take on quasi-governmental functions, and we can hold them morally responsible for their actions. I suspect that this can get extended to educational organizations that seek to shape politics. I used Greenpeace as an example in the paper. Think about cancer for a moment. Is the cure for cancer an existential threat to the American Cancer Society (ACS)? If so, are potential cures for cancer threats to the ACS?
Threats can take many shapes and forms depending on the organization and the threat. One person’s cure could be another person’s existential threat.
We can potentially see this unfold in Ukraine.
An organization needs to understand itself and any partners before it can truly understand the threat. Often the threat will attack something the organization may not initially think is critical. An organization may have strong capabilities but need a projection platform to employ them. If the threat takes away or degrades the projection platform, does that negate the strong capabilities if the organization cannot project them to the critical place and time?
Capacity is perhaps the most dynamic component. The key question is how long can the threat manifest the capabilities? Problems may arise from consumables (think the German constraints with fuel during the Battle of the Bulge), losses during execution, or simply a small amount of the capability to begin with. So, the second question is, Does the threat have enough capability to achieve the intent? Or do they just need it for leverage or as an opening move that allows potentially lesser capabilities to be effective? Potentially, the structures that sustain a capability are a capability in themselves. Think about the ball-bearing factories and oil refineries the Allies attacked during WWII.
Threat assessment must look not only at the individual components but also at how they relate to each other and shape and influence each other. These relationships could define separate scenarios or sub-scenarios.
In some ways, this reminds me of some of the complex models I built on spreadsheets that required iterating the calculations several times until they stabilized. I got to know the F9 re-calc key very well. We may need to similar iterative approach to assess how the components interact with each other. This process could lead to the development of several scenarios that rely on the same basic capabilities.