
Threat Part 3: Iterative Process and Scenarios
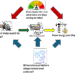
Part 2 discussed an iterative approach to threat assessment and scenario development. This part develops an iterative process as shown in the figure below, as well as an introduction to threat scenario development.
The threat development process is a continuous loop designed both to add new information and to update for changing socio-cultural effects and risk profiles. For example, different socio-cultural and/or risk profiles could create multiple scenarios, based on the same capability and capacity information.
Information collection should be open and continuous, with an eye to spotting key changes and new capabilities. It should be an all-source approach to collecting as much information and even data as possible. With new storage and data wrangling techniques and technology, we can collect and store far more information than ever before. This is important as we may gather information on key changes that we may not be specifically looking for.
The information then needs to be processed. This is primarily a data wrangling and repository operation. Processing looks at data duplication, data errors, data relationships, and effective storage to assist the analysis phase. We should also assess and categorize additional sources for reliability, quality, and relationships with other sources. Data duplication is not a bad thing. Duplication from several sources might add to the reliability and provide different dimensions to the information.
The goal of information analysis is to turn data and information into knowledge and actionable information. In the case of threat development, actionable information leads to new insights into the threat and potentially new threat scenarios.
Scenarios show both the threat capabilities and how they intend or at least could use them. There are three kinds of scenarios:
- Most likely. This scenario depicts what the threat can do today based on known capabilities, capacity, intent, socio-cultural factors and expected risk tolerance. This scenario or family of scenarios, depending on geographic location and perceived intention, trainers should use them in live, constructive, and virtual training from the platoon and higher echelons, with the scenario tailored to the echelon.
- Most dangerous. Trainers should use this scenario or scenario families in wargaming to assess the US ability to deter and/or defeat the threat. What do we need to defeat it? This ability needs to include power projection requirements, access, and socio-cultural dimensions.
- Wild card. This scenario type is geared towards experimentation. It may include threat capabilities that are expected, but not yet manifested. The longer the time horizon, the greater the need to think out of the box and enter the domain of the Mad Scientist.
The next part will cover scenarios in greater detail.
Once the threat team develops scenarios, they need to go through a validation and approval process. The validation process should:
- Do we understand the threat in enough detail to develop and train threat emulators?
- Have we sufficiently described and developed the threat?
- Can we train sufficient emulators that understand the scenario and can properly emulate the threat’s capabilities and tactics, techniques, and procedures (TTP)?
- Can we support training, wargaming, and experimentation at all required levels?
Once the scenarios are validated, they need a final, formal approval process to ensure key leaders understand them and the requirements to use them.
Upon approval, we need to deliver the threat. That means we need to:
- Train and validate threat emulators.
- Deliver documentation of the threat and the scenarios, as well as potential situation and requirement specific.
- Ensure the threat order of battle is prepared and ready for simulations.
The last two phases are execution and assessment. From the threat perspective, we assess not friendly performance, but how well the threat was replicated and emulated. Did the threat emulators use the appropriate capabilities and TTPs? Is the scenario an effective training vehicle?
The threat team then reviews the assessments and makes changes as required and potentially providing insights and recommendations for further information collection and scenario refinement.





One Comment
Pingback: